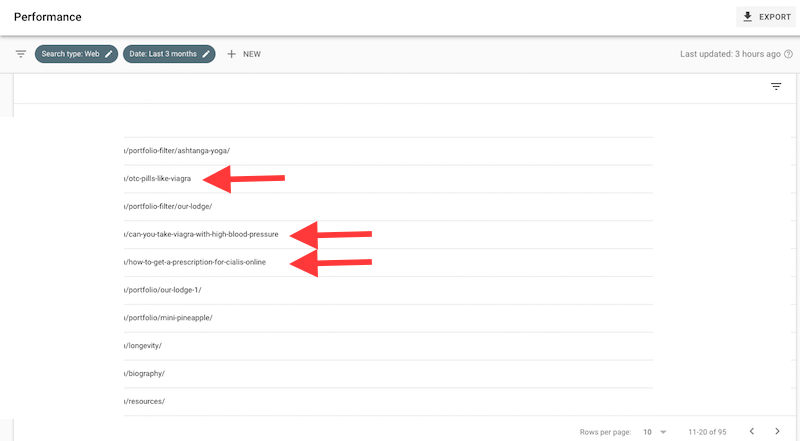
While doing some SEO for a client’s website, I noticed a weird URL coming up on Google Search Console: can-you-take-viagra-with-high-blood-pressure
I thought I’d share how to remove spam backlinks from a website in case you run across the same issue.
Spam links may come in various forms and are also called toxic backlinks, fake code, injected code, injected spam links, fake jQuery injection, backlinks spam, spam link injection….the list goes on.
Anyway, my client runs a luxury raw food yoga retreats in Ecuador’s cloud forest (which I can personally recommend!), and is definitely not going to be posting this type of content.
How do I check my spam backlinks?
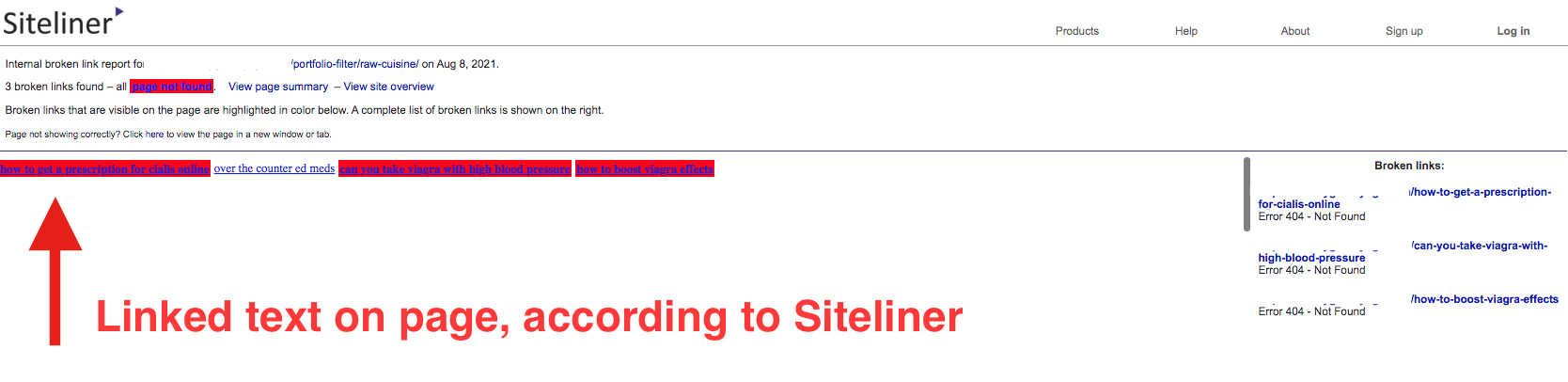
I initially noticed the spammy backlinks on Google Search Console, but to double check, I went to siteliner.com (FYI, Siteliner is also great to identify duplicate content on your website) and found that the same link appeared, along with 2 others, as broken links:
– how-to-get-a-prescription-for-cialis-online
– how-to-boost-viagra-effects
– can-you-take-viagra-with-high-blood-pressure
Clearly we were dealing with some kind of malicious activity; the site had been hacked.
Fortunately, it was hacked before I started working on the site.
Though the broken links were supposedly located on one of the pages, when I went to the page itself, I couldn’t see the links or find them in the source code.
This means we were dealing with spam links which are injected into other elements of your code, like jQuery.
Backlinks spam = black hat SEO
Backlinks spam is a black hat SEO technique to help other sites rank higher. When hackers inject this code onto your page, Google is tricked into thinking your page is a referral page or backlink for the injected URL.
These links often go unnoticed and may not affect the rest of your site, but they are nonetheless malicious and I’m pretty sure my client doesn’t want these viagra prescription links on her site.
Also, this type of hacking is particularly common on WordPress since many people aren’t frequently maintaining their site.
“It’s very easy to check what version of WordPress a site is using as well as detect a particular outdated plugin…[There] are scripts hackers can run that simply trawl the internet looking for particular vulnerabilities in every WordPress website they can find. [Some are] so advanced now that they have user interfaces and full automation, you can just set them off and even automate the hacking process itself.” – BuzzFeedNews
Well if that doesn’t scare you I don’t know what does.
This is why you might hire a website manager that frequently logs onto your site (every other day, 3x/ week) to update plugins, the theme, the version of wordpress, make backups, run security scans and delete any unnecessary plugins and themes.
That said, websites on other content management systems can absolutely be hacked too, like Joomla or Drupal. I still prefer WordPress, despite these security issues.
Cool, so what now?
Double check that your site has been hacked with spammy links
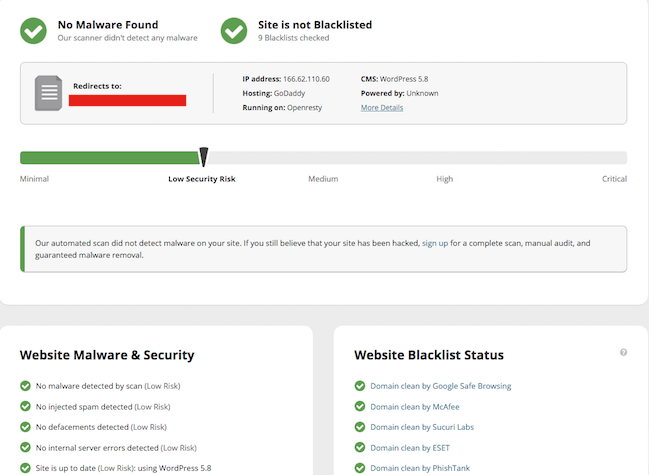
To double check that the site has been hacked, I went to https://sitecheck.sucuri.net/ pasted in the url and clicked scan.
Interestingly it returned with no results, which is odd since Sucuri is a top-notch, reputable, malware and security tool. Hmmmm, not so secure-y after all…
Next, I downloaded Wordfence security plugin for WordPress and scanned the site.
The results returned with 12 critical issues, the majority of which were malicious files. Some were outdated plugins.
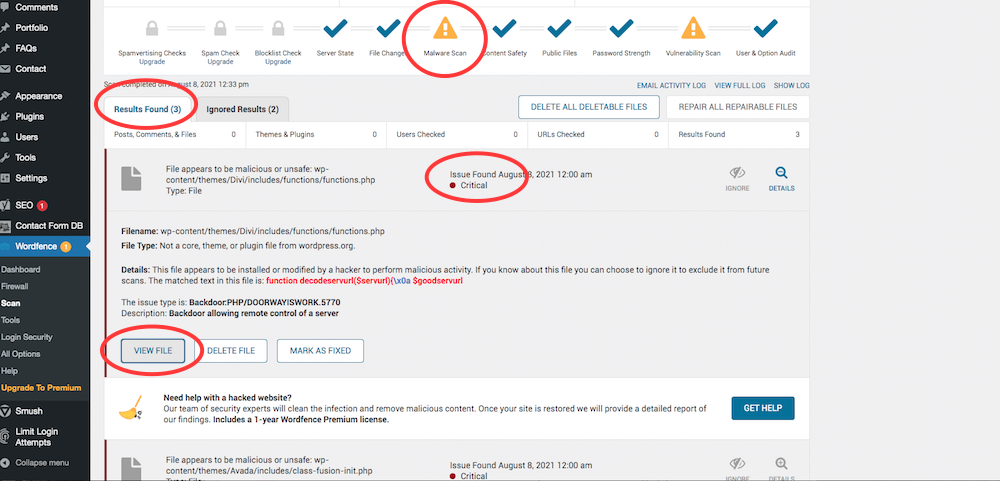
Wordfence lists all the malicious files, but unless you’re paying for Premium, you have to manually deal with the files (or the sections of code).
Wordffence offers you the option to “delete the file”, which has worked for me in the past, but there’s something about manually putting in the trash that puts my fears to rest.
To locate the file, go back to the Wordfence results pane, click on a critical issue and take note of the file location.
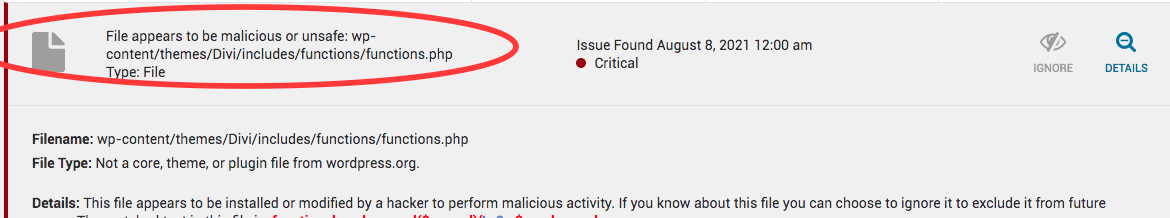
You can click on the “view file” button and, ideally, you have the option to click on “view differences”. However, this option isn’t always available (it might have been removed with an update to the free Wordfence version).
If you’re able to “view differences”, you can easily identify whether the entire code is affected, or just a section.
When you click “view file” you’ll probably see some questionable code.
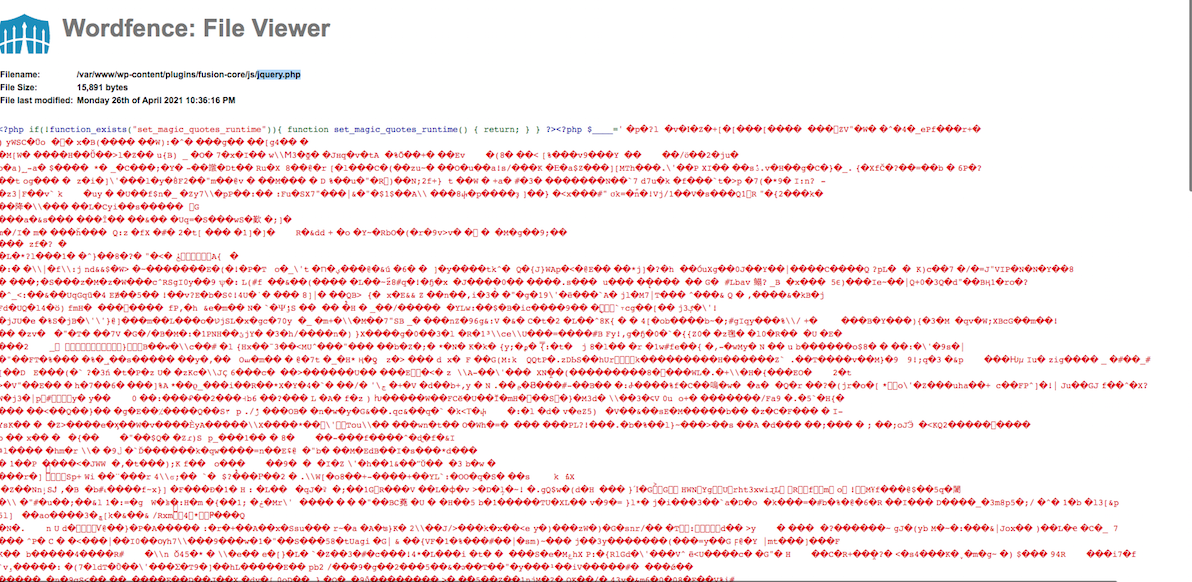
If it looks convincing (this one definitely does, but some look pretty normal), head over to your cPanel on your hosting provider.
(NOTE: If this last step starts to make you feel uncomfortable, you should consider hiring someone (Hi. I’m right here.) to help you with this process and PLEASE DO NOT hire off of Fiverr.
Side story: I once hired a web developer off of Fiverr to fix an issue with WPML and ended up with even more malware on my site. Instead of 12 critical issues, I literally had over 1200 injections of malicious code and ended up deleting the entire site and re-installing a backup. NIGHTMARE.)
Ok, so now that you know the file location, locate your file manager in cPanel and navigate to the location of the malicious file.
Very important: Before you continue, make sure you have fully backed up your website! On WordPress I use the Updraft Plus plugin.
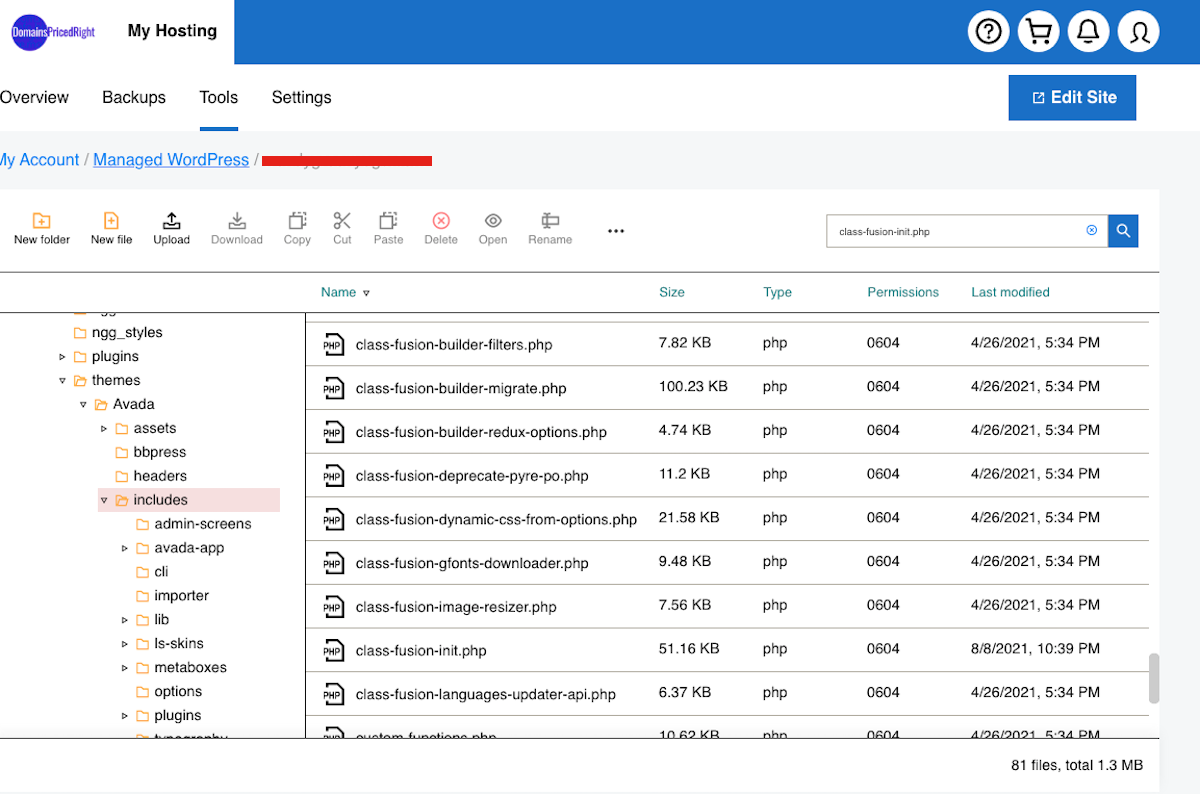
Download the malicious file and open it with Sublime Text 4, which works better than TextEdit for .php files.
Edit out the code, save the file and re-upload it to the same folder.
If the entire file is corrupt, delete the file UNLESS it seems important. For instance, iff you’re staring at your css file, definitely DO NOT delete it.
Always download the file from your file manager before deleting it. If, after deleting it, your site breaks, re-upload it to file manager.
You can also input the filename on Google to understand what it does and if it’s vital. Generally speaking, don’t delete the file unless you’re pretty sure it isn’t vital.
Regardless, always make sure you’ve backed up your site.
Again, this is where you might benefit from hiring a web developer with experience doing this type of clean-up.
Basically, you do this for all the files (in my case, all 9 files after ignoring the plug-in warnings) and then run a new Wordfence scan to see what comes up.
Hopefully nothing comes up 🙂 Sometimes it takes a few scans and deletions to result in a clean scan though, be patient.
How do I stop spam backlinks in the future?
To prevent future backlinks spam attacks, Wordfence is your friend.
Another useful tool is WP Hide Login, which changes your login page to anything you want.
With WP Hide Login, instead of mywebsite.com/wp-admin, I would log in to mywebsite.com/holyguacamole, which is a url that hackers won’t be able to find nearly as easily.
That said, only download necessary plugins to your WordPress site. Since WP hide Login is for security, I consider that necessary.
Conclusion
Don’t underestimate the power of hackers. Cyber security has reached new levels of sophistication and automation, it’s nuts. And once you’re hit, I promise you won’t hesitate to pay an annual fee for a Premium account with Sucuri or Wordfence.
Back on track: To prevent a fake jQuery injection or other spam links on your website,
1. Download a security plugin like Wordfence or Sucuri, pay for Premium if you can afford it
2. Regularly maintain your site, updating plugins etc and delete anything (theme or plugin that you don’t use)
3. Regularly scan your site
4. Regularly backup your site
This is how I remove spam backlinks, but let me know if you have a better process!